Other topic
3 Modern Email Security Threats You Should Know About
In 2020, we saw a global switch to a remote workstyle. Some industries managed to adapt in a blink of an eye, while others struggled to implement all necessary changes and keep up with the new rhythm.
However, there is one thing both these categories have in common - the increased risk to their email security.
Since businesses started relying on cloud email more, cybercriminals became more persistent in breaking through the defenses to gain access to valuable financial information data or install ransomware. According to the Phishing and Fraud Report 2020, the number of phishing attacks grew by 220% at the pandemic's peak. Scammers and phishers made it clear that they don't care about ethics and would gladly exploit any vulnerabilities in your network.
Resisting their plans and schemes is a group effort. While email services and internet services providers work on additional measures for intercepting and penalizing cybercriminals, users worldwide must show extreme awareness of the latest trends used by phishers and fraudsters to slither past the mailbox's defenses.
This blog post will help you do your part and be more aware of the modern dangers that threaten your email data.
1. Ransomware-as-a-Service (RaaS)
RaaS is the latest and the most obnoxious security challenge that organizations have been dealing with since 2020. It works exactly as it sounds: a group of malicious actors with the knack for creating harmful ransomware sell their harmful programs to a lot less skilled cybercriminals, letting thousands of ill-intentioned people without any technical background commit cyber extortion. So, you can already see the problem: RaaS made it much easier to spread chaos and launch malicious campaigns. Around two-thirds of ransomware attacks were attributed to RaaS in 2020. By 2021 the appetites of RaaS-using crooks grew even higher, going for more expensive ransoms and continuing to compromise organizations.
How do you protect yourself from RaaS?
Much like with any ransomware, the best defense against programs designed to assault your network and steal your data is proactivity.
- Network segmentation. All servers, apps, and databases that store sensitive data, should be isolated from other servers. Additionally, third-party users should access data through isolated portals instead of those your employees use. You must ensure that there is no easy illegitimate path to your data by constantly reviewing your architecture and instantly removing any loopholes.
- Endpoint protection. You must install advanced anti-malware to all devices you use to connect to your network and regularly upgrade it because new versions carry new ways of protecting the system from ransomware attacks.
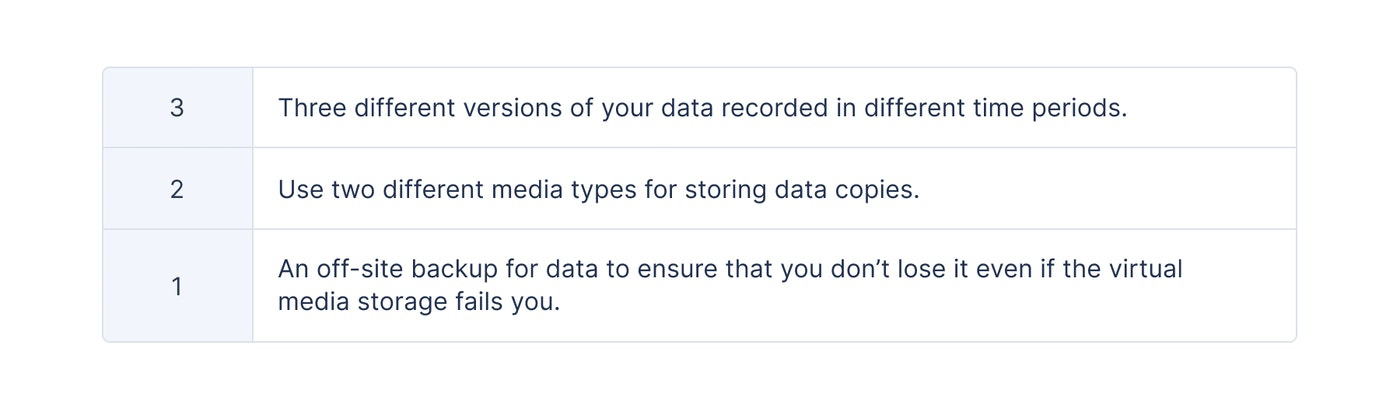
- Data backup. Ransomware operates by holding valuable data hostage. Having a backup of that data allows you to soften the blow and not be a victim of extortion. You must regularly back up your data by following the famous 3-2-1 data backup and recovery strategy.
The important rule of data backup is to never use the same cloud service or media for storing your copies. That defeats the entire purpose of the 3-2-1 strategy.
2. CEO Fraud
While not new, CEO fraud phishing has been on the rise since 2020. This method is based on the impersonation of a company C-level executive to steal login data, business data, or even corporate funds.
CEO fraud phishing works the following way: a user gets a message that a credible person allegedly sent from their workplace: their CEO, chief marketing officer, or chief financial officer. The message asks the user to help with a work-related transaction, such as a wire transfer to a vendor. Of course, there is no vendor, and the company's funds get sent to the fraudster's account.
CEO fraud phishing is also used to attain private employee information and sensitive company data by targeting HR managers and IT teams.
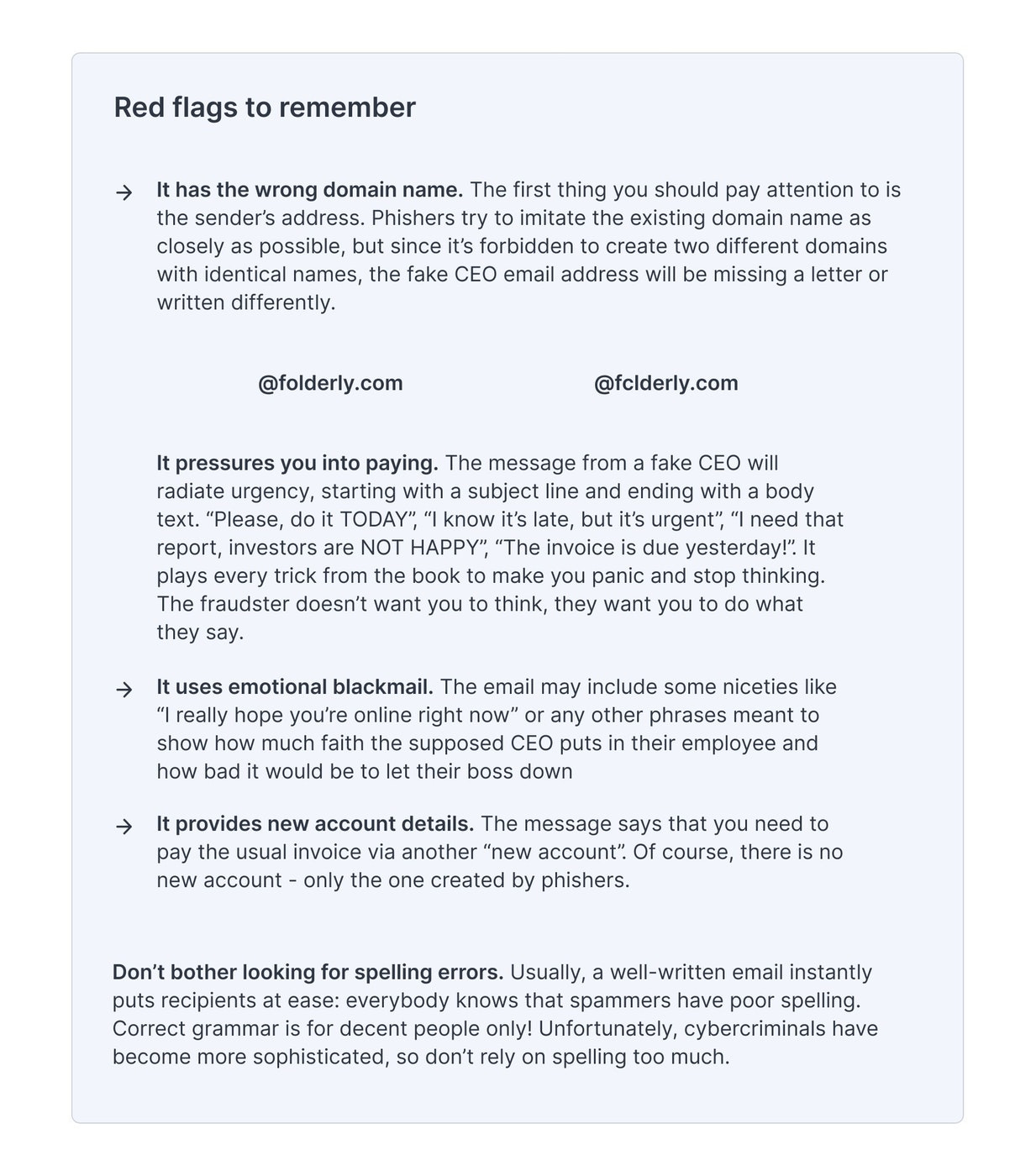
CEO fraud is usually committed by either using a compromised email account of a C-level executive or creating a fake domain that mimics the official's name. On average, each CEO fraud cost a company around $75,000, while the reported loss for businesses that suffered from this impersonation scam between 2016 and 2019 was $26 billion.
How to protect yourself from CEO fraud?
- Advanced mailbox protection. All your mailboxes must be protected by a smart email security service that can verify the sender's email address by referring to public records and scanning attachments for malware.
- Employee awareness. Teaching your employees to treat every incoming email with caution will keep your funds safe and your sanity intact. Every newcoming team member must be instructed about the dangers of CEO fraud and taught how to tell an actual email by a C-level executive from a fake one.
3. Cloud platform vulnerabilities
The popularity of Google Workspace, Office 365, and other cloud platforms became a double-edged sword for many businesses. While these services are of great help when building a network and communicating with in-office and remotely working teams, they lack security, making businesses more open to all kinds of digital threats.
We're talking about malicious hackers gaining access to the private information of your employees, stealing login credentials, or manipulating your staff via social engineering and brand impersonation. For example, they gain the list of companies you try to reach and pretend to be them to make you open an email or download an attachment.
How to protect your cloud platform of choice?
- Extra security measures. This is the only piece of advice you'll ever need regarding the safe use of Office 365 or Google Workspace. Don't rely on the built-in features - make a phisher's day harder by encrypting your data and adding new levels of security. For example, tools like Virtru provide reliable data encryption that keeps your information shared in Gmail and Google Drive safe from phishing.
- Teach your employees' safety discipline. Don't let your employees be careless about the way they manage their mailboxes and sensitive data. Tell them about the basic rules they must follow whenever they access the network and monitor their compliance with these rules.
Takeaways
Cyberthreats became more sophisticated and, to everybody's horror, more mainstream. With the appearance of RaaS, the amount of ransomware attacks is guaranteed to increase within a short time. Meanwhile, networks became less stable due to mass migration to platforms and adjusting to the new norm.
Nowadays, it's imperative not to make phishers, and ransomware senders feel at home and give in to their appetite. Instead, every legitimate sender and business owner must work on their defenses and stand their ground.
- Trust no one. Scrutinize every email that falls into your inbox. It doesn't matter if it says it's from your boss, investor, mom, or Elon Musk. Study it closely, look for red flags. If the content looks suspicious, contact the sender by phone or message them asking if they sent an email to you. Wear your tin foil hat with pride.
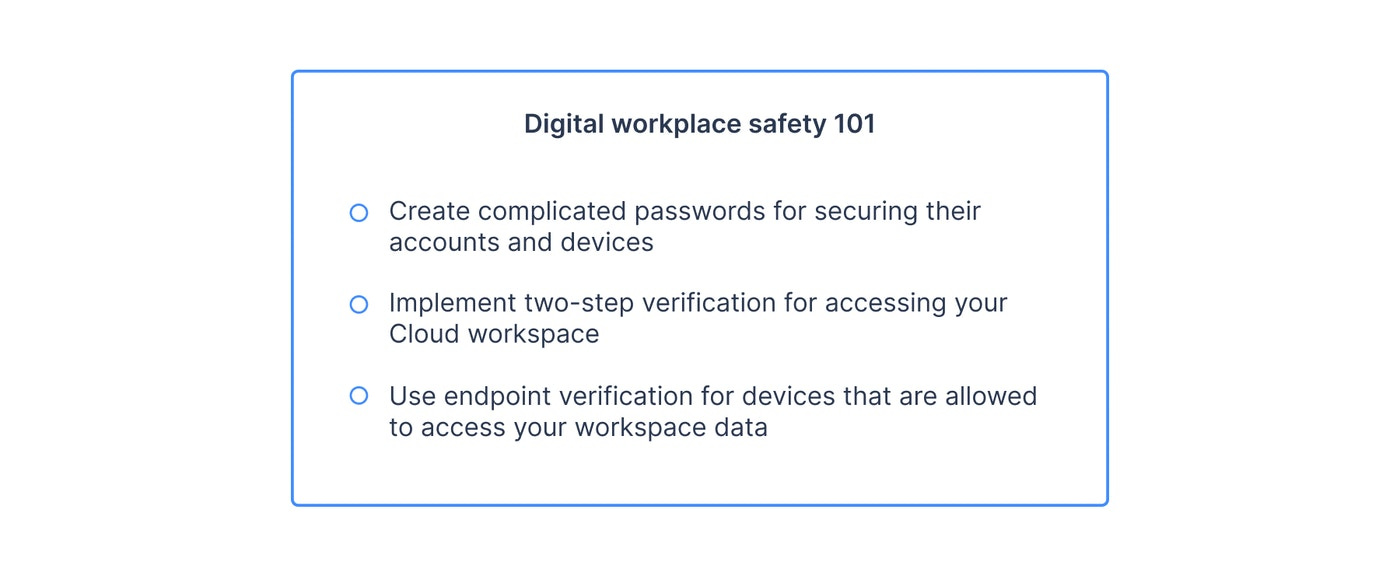
- Use high-quality anti-malware solutions. It's not enough to install a random antivirus and call it a day. Use anti-malware that provides endpoint protection and update it regularly.
- Back up your data. Go all the way to make sure that you can quickly recover any valuable data at any point. Store it on different media and off-site storage for extra protection, don't put all your trust in just one service.
- Make cyber-safety a part of your business culture. The human factor plays the most prominent role in preventing security breaches and data leaks. It would be best if you nurtured the culture of responsibility and awareness among your employees. Include safety guidelines and lead by example, implementing new security measures whenever it's possible. Discipline and the ability to think critically are the most powerful boost to any security software.
To close this post off, we'd also like to remind you that many modern security solutions authenticate the sender by checking both DNS records and public records. The more authentication protocols you have, the harder it is for phishers to compromise your mailbox.
Dedicate some time to ensuring that all your email authentication protocols are in place and contain accurate information about your domain. Don't know how to check your settings? Folderly can run a quick test of your domain and notify you if there is a problem with your DNS settings.
How to sync Facebook Ad Account time with Facebook Lead Ads?
I'm using apiway to update my facebook leads on a google sheet. The only problem I'm facing is the time zone. The ad account time is set on GMT +05 but the time I'm getting is GMT +0000. How can I sort this ?
Facebook leads don`t update the new Forms .. and I can`t add new FB page in the same account .. How can I do it?
Facebook leads don`t update the new Forms .. and I can`t add new FB page in the same account .. How can I do it?
How to connect bitrix24?
I get an error when connecting the application
403 This action is unauthorized.
Leaderboard

Recommended